Penetration Testing
New security breaches and ransomware attacks occur every day and can be thwarted by maintaining good security and systematic testing–RubinBrown can help.
Penetration Testing
New security breaches and ransomware attacks occur every day and can be thwarted by maintaining good security and systematic testing–RubinBrown can help.
RubinBrown Penetration Testing services include a combination of vulnerability scans, penetration testing, web application security assessments, and custom-designed manual testing. Vulnerability Management is used to identify out-of-date software, missing patches, insecure configurations, and misconfigurations before they can be exploited by attackers. It is that extra bit of vigilance to double check cyber security hygiene—make sure you are as up-to-date you think you are and your patching and configuration processes are working as intended.
Every day, new security breaches and ransomware attacks are announced from out-of-date patches, configuration errors, or access control issues. All of these attacks can be thwarted by maintaining good security hygiene and then systematically testing to ensure everything is working as planned.
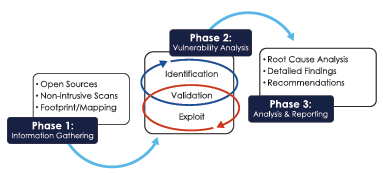
You can start with basic network vulnerability scanning and then build on the program, adding in authenticated scans, security hardening scans, penetration testing, and web application security assessments over time. The following table provides a basic approach to the testing and frequency for a basic vulnerability management program.

Our penetration testing services focus on manual testing supported by automated solutions. Influenced by penetration testing guidelines, standards, and our extensive experience, they meet requirements for PCI DSS, NIST, and related standards.
We perform dynamic application security testing (DAST) for our web application security assessments. Dynamically testing the code focuses on realistic attacks every web application connected to the internet will experience. We use a combination of the Open Web Application Security Project (OWASP) tests, NIST, PCI DSS, and checks we have collected over decades of experience in our assessments to test vertical (privilege escalation) and horizontal (user-to-user) security.
The results from these activities feed security metrics, inform patch management and administrator effectiveness, and, when integrated as a Vulnerability Management Program, provide an appropriate level of vigilance to protect your organization from attacks.
